By Gwen McEvoy
— April 27th, 2022
It’s early on a Monday morning. Your mind is easing its way toward work, yet you’re resistant, still enjoying the freshness and quiet of your walk.
Ping! You hear the familiar text message alert from work. So early, you think, grimacing as you pull out your phone to see who or what it might be. It’s from our CEO, David Levin. It must be something very important indeed!
So, you respond, at least initially, before ghosting “David” once you realize what’s happening.
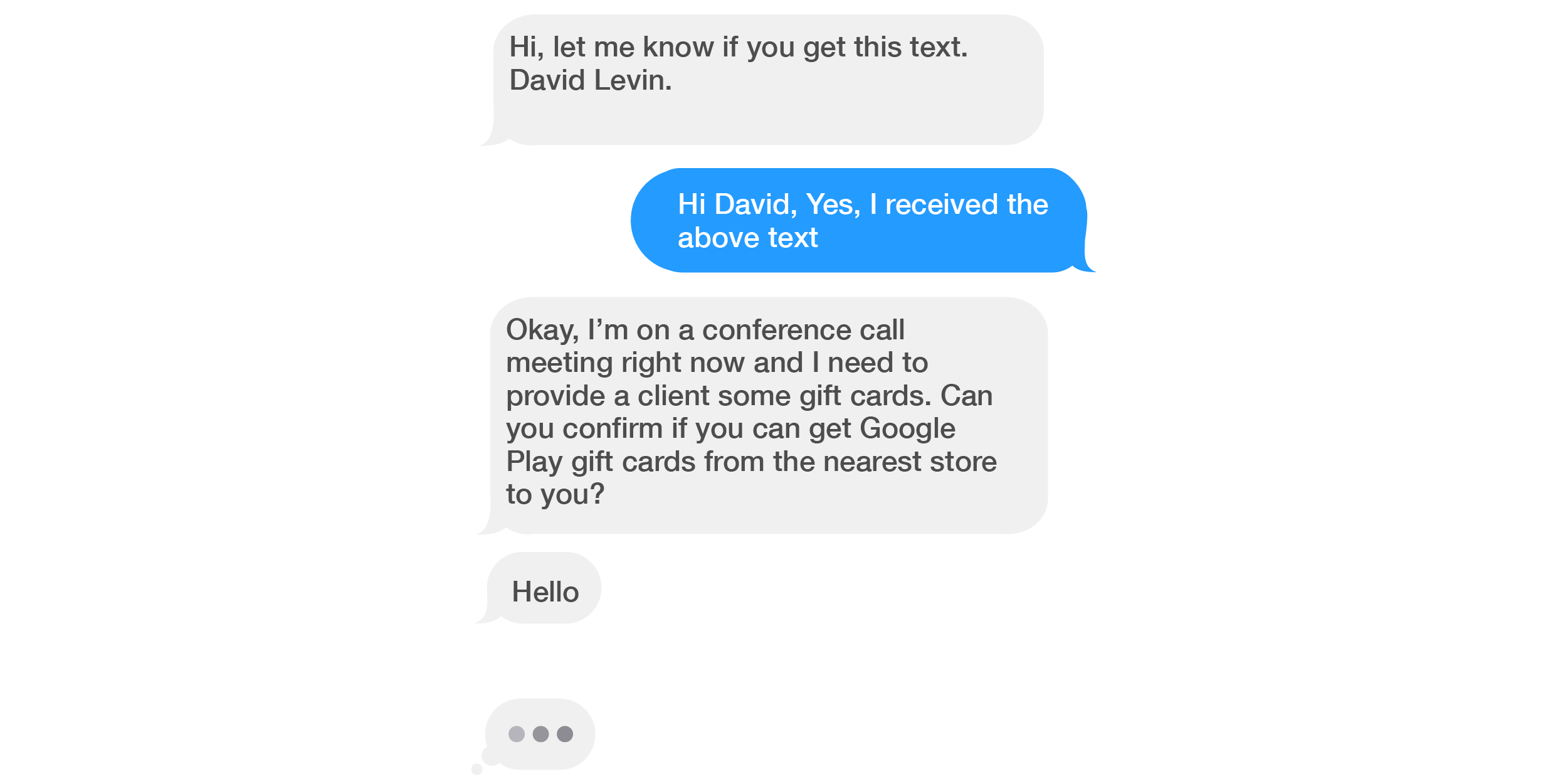
The screenshot above is a real and recent example of “smishing” which, along with “phishing,” is a type of “social engineering.”
In the realm of cyber security, social engineering involves an attempt on the part of a “bad actor” to persuade someone to provide their personal or confidential information for purposes of fraud (including maliciously gaining entry to a company’s network).
The perpetrator might use a phone call, an email or text message, or even an in-person visit to psychologically manipulate the recipient into taking some action—by means of, for example, invoking authority, urgency, fear, or other emotion.
(Social Engineering and its complexities will be the topic of a future blog.)
This popular scam (requesting purchase of gift cards) is probably familiar to many, but certainly not to all. In this instance the bad actor is using “authority” to try to manipulate the recipient into carrying out their request; after all, it’s hard to say no to the boss.
What happens if you do decide to assist? Maybe it’s near the end of the quarter and you’re aware that many folks in the company are busy trying to land that last deal.
Depicted in the screenshots below is a part of a recent exchange between “Andrew O’Shaughnessy” (not the real Andrew, founder of Poppulo, of course) and an employee. “Andrew” initially emailed the employee, requesting their What’s App number.
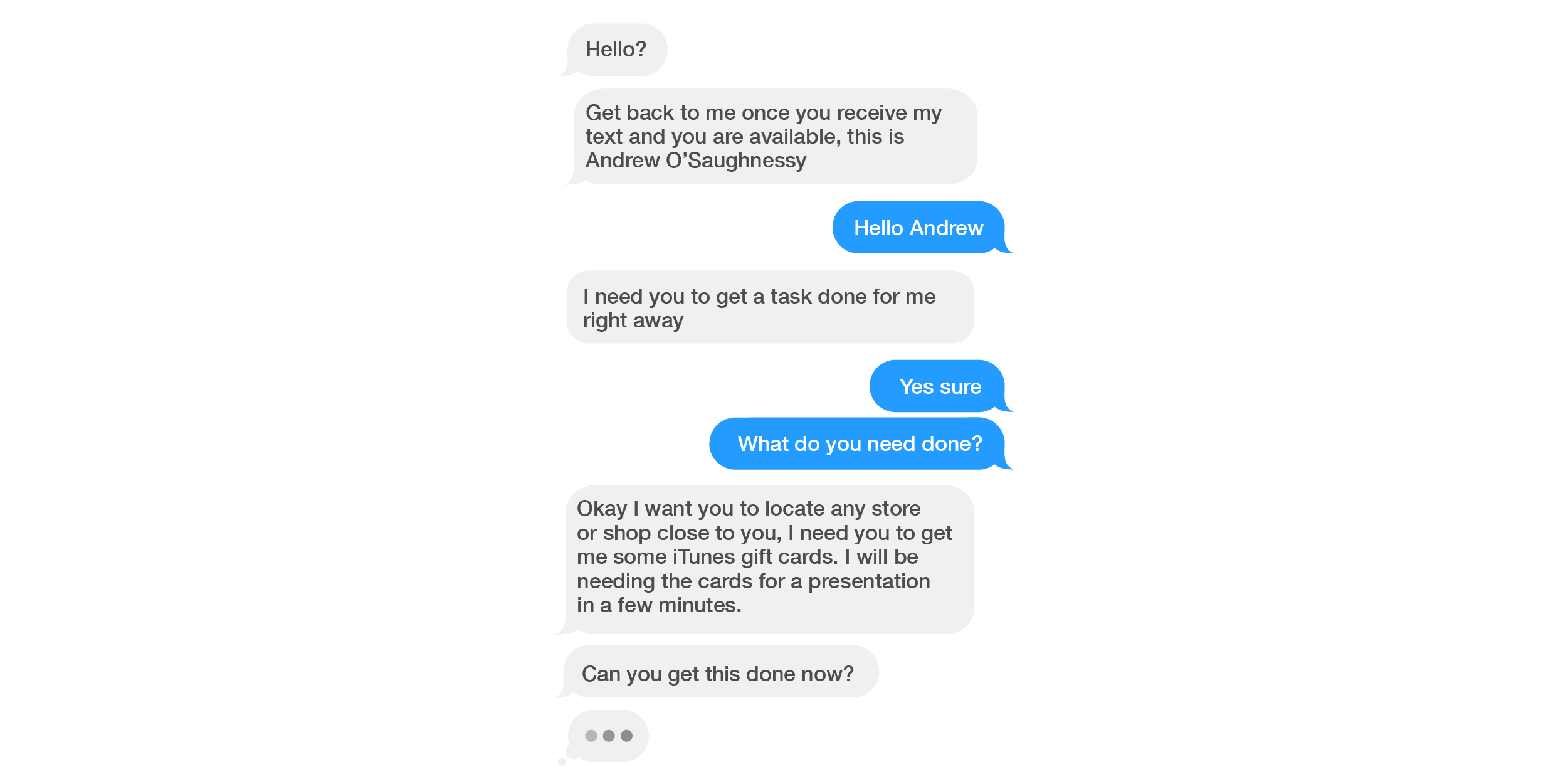
Here, “Andrew” leverages not only “authority” but also “urgency” in his quest to manipulate the employee into purchasing iTunes cards “right away.” Why he would need these for a “presentation in a few minutes” is unclear, but the employee takes the request seriously.
As the conversation continues, “Andrew” provides the number and denomination of electronic cards he needs. When the employee states they don’t have the necessary funds in their bank account, “Andrew” pushes harder: “you need to find a way to get this done…. I will advise you to get a loan from a friend or relatives,” adding that he’ll reimburse the employee immediately upon completion of the task.
Again, luckily, as in the scenario noted earlier, this employee had doubts about the request and contacted their manager prior to taking any further steps.
It’s easy to see, though, how one might become caught up in the moment and respond to the authority and urgency invoked in the request.
What, then, should you do when you receive a smishing (or a phishing) request—whether from a bad actor pretending to be your “boss,” “co-worker,” someone outside the workplace, such as your “uncle” who lost his wallet while visiting NYC, or a bank or government rep?
They might ask for gift cards, or for something else of current or potential monetary value, including cryptocurrency, a wire transfer, your credit card or Social Security number.
If possible, contact the requestor directly using another means of communication (telephone, Facebook, Twitter, and so on) to confirm their identity. Check the requestor’s number against your existing Contact entry if you have one. If the initiator is a business, contact it directly or log into your account separately.
Check with a co-worker or friend for their opinion on the logic of the request. Don’t click on any links in the message or provide personal information until you’re sure the request is legitimate and not a scam – even if the requestor states you “must do it right now”—or else.
Social engineering attacks, including smishing and phishing are on the rise, according to cyber security professionals and researchers.
Rather than reacting quickly to a smishing (or phishing) message you receive, take a moment to put on your critical thinking cap, assess the sender, phone number, or email address, and the logic of the demand or request.
Additional information on smishing and other types of social engineering:
https://www.social-engineer.org/
